Secure Android Application Development Tips
In Android Operating system, there are lots of security features which will protect your applications.
The common security threat of Man in the middle attack, will help attackers to initiate an attack from a mobile application. This may of a small mistake like adding log of sensitive data.
After development of an application it is better to do a Penetration testing. There are lots of tools and services for penetration testing and vulnerability testing. In this post I would like to give small idea about how to avoid vulnerabilities and security holes in our android application while development. As developers we should aware about the best practices of secure application development.
Android developer page contains the security best practices and security tips, the developers should follow while development. The best thing is to keep these basic tips in mind throughout the development. Then we can reduce the number of vulnerabilities and security issues inside the application. There are few basic tips to be followed on creating secure applications and those are as below.
The common security threat of Man in the middle attack, will help attackers to initiate an attack from a mobile application. This may of a small mistake like adding log of sensitive data.
After development of an application it is better to do a Penetration testing. There are lots of tools and services for penetration testing and vulnerability testing. In this post I would like to give small idea about how to avoid vulnerabilities and security holes in our android application while development. As developers we should aware about the best practices of secure application development.
Android developer page contains the security best practices and security tips, the developers should follow while development. The best thing is to keep these basic tips in mind throughout the development. Then we can reduce the number of vulnerabilities and security issues inside the application. There are few basic tips to be followed on creating secure applications and those are as below.
- Storing Data - Should not store confidential data inside devices.
- Permissions for application - Reduce risks by not requesting the sensitive permissions.
- Networking - Use secure communications over network.
- Input validation - Proper validation required for input such as network data,file access, IPC return data.
- Handling user data - Avoid of storing or transmitting user sensitive data if possible.
- Using Webview - Consider about cross-site-scripting.
- Using Cryptography
1) Storing Data
As per requirements of the mobile application, we have to store data inside the mobile devices. That can be as a file, database record or some other format. If the data you are saving inside the mobile device can be accessed by other applications, then there are concerns about the security.
There are three main ways to save data inside a device. That is Internal Storage, External Storage and ContentProviders.
There are three main ways to save data inside a device. That is Internal Storage, External Storage and ContentProviders.
Saving data in Internal Storage will give protection inside an application. Because the data will be saved inside the application context and can be accessed by only the application itself(Handled by Android Operating System). In this case the data will be saved inside the sandbox(private storage) of the application. The data saved in internal storage can be compromised on IPC(Inter Process Communication). Other applications can access data using IPC and there are no such way to limit the access for a particular application if we use MODE_WORLD_WRITEABLE and MODE_WORLD_READABLE (Currently these two have been deprecated from API level 17).
Saving data in External Storage is the other way of saving data in devices. The external storage can be a SD card and this content can be accessed by everyone, including other applications and users. Therefore we have to be more careful and should not save user sensitive data to external storage.
The other way of data saving is ContentProvider's, where this data is accessible to own application or authorized application only. Authorized application's are, the application that will have the correct Content URI of the provider. The main advantage of Content Provider is that to avoid SQL injection to application data source. Content Providers uses parameterized methods to do the database operations and will never executes raw SQL queries.
Simplest SQL injection example is 1=1 in a where clause, because 1=1 will always be true.
SELECT * FROM Users WHERE UserId = 105 or 1=1
2) Permission for Application
It is recommended to minimize the permission request for an application. The applications, which contains sensitive permission access will help attackers to misuse the permissions and do damages to the system. Always try to use the system defined permissions, as they will cover most of the required situations. If by any chance you needed to create a custom permission, make sure to use "signature" protection level. With this protection level, the permission will transparent only to the applications signed by the same developer.
3) Networking
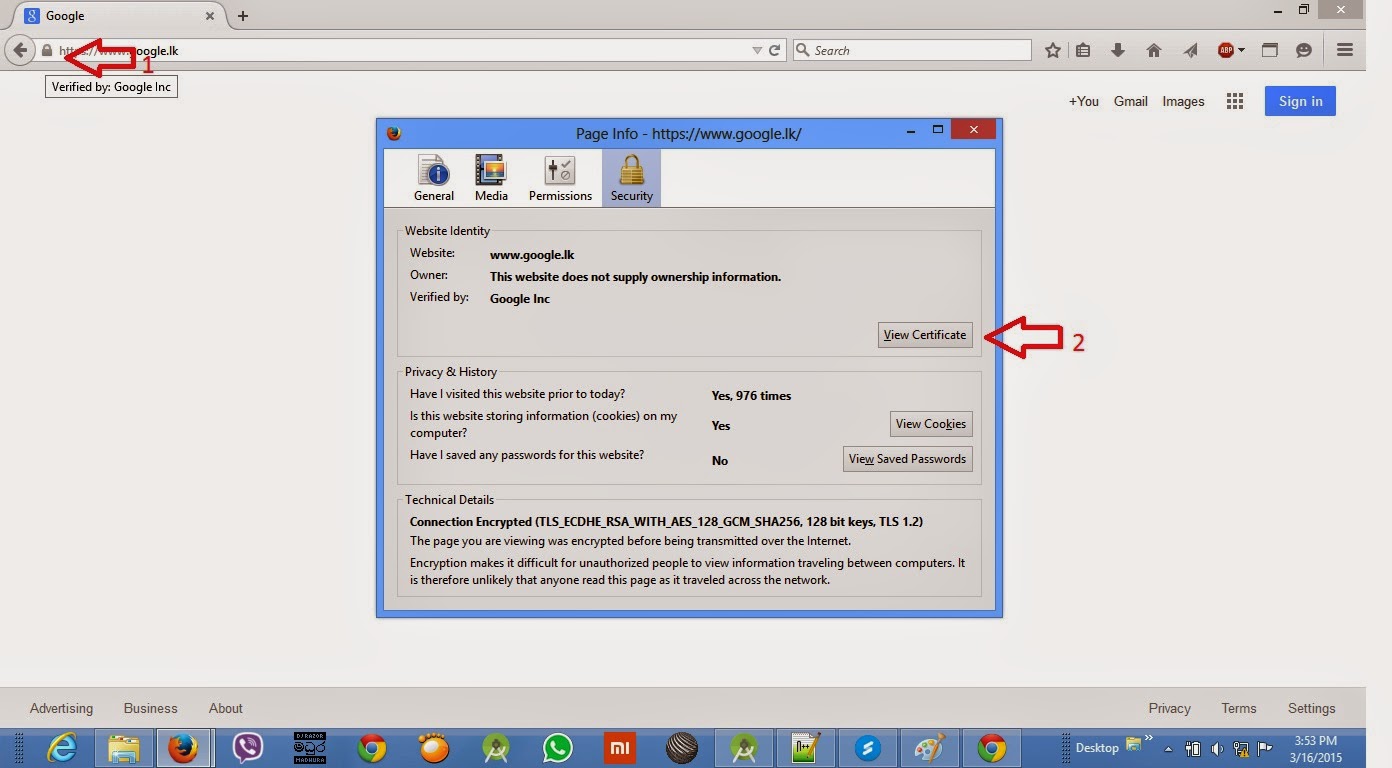
Network communication between the mobile app and server needs to be encrypted. If not, an attacker who is able to intercept the network traffic has immediate access to all information sent over the network. It is also possible to manipulate the network traffic via man-in-the-middle attacks. This will compromize all the user data to athe attackers and will be a big security fall of the system. Therefore it is recommended to use HTTPS instead of HTTP for client-server communication. HTTPS will enable a secure channel between client and server. Even though HTTPS is more secure than HTTP, some attackers can break HTTPS by using the Certificate Authority. Mainly the attacker will replace the trusted certificate of the client by his own certificate(which is a valid and authorized by Certificate Authority) and all the data will be signed by his certificate. He can get the data as he's having the private keys with him.
4) Input Validation
There is a possibility of security issue on the data read by applications from file system, server response or IPC return data set. When it comes to javascript and SQL queries, they contatins plain strings and anyone can update and make the string vulnerable. By using a Webview inside the application with javascript enabled can be an security issue such as script injection. As we have discussed in above category(Storing Data) an attacker can change the SQL string and executing that directly will do SQL injection to the data sources. There are several categories of input validations, a common one is URL redirection to untrusted site inside Webviews[URL Redirection to Untrusted Site ('Open Redirect') CWE ID 601].
5) Handling User Data
Be careful on saving user specific sensitive data on devices such as usernames , passwords. It is not a good practice to save sensitive data as shared preferences or databases without encrypting. Even if confidential information were stored encrypted in these files, it would be trivial for an attacker to retrieve the encryption method and secret key by decompiling the mobile application. Therefore sensitive information should not be stored on the device when possible.
It is recommended to take advantage of native Android library functions to encrypt files on the device. To provide protection for sensitive data, it is recommended to choose to encrypt local files using a key that is not directly accessible to the application. For example, a key can be placed in a KeyStore and protected with a user password that is not stored on the device. While this does not protect data from a root compromise that can monitor the user inputting the password, it can provide protection for a lost device without file system encryption.(Source Google Developer Site)
6) Using Webview
In android applications we may have to enable javascript inside the Webview to work scripts. If it's not required, then never call setJavaScriptEnabled(). As enabling javascript may cause to have cross-site-scripting, which is a known security issue in most web based applications. Best practice is to handle all the javascript by the application level and use a javascript interface to execute them or use a javascript engine such as Rhino.
7) Using Cryptography
As explained in Handling user data section, it is a best practice to use the cryptography to secure local files. This can be used on client-server communication as a second level protection. It's better to use crypto and compression while doing the data communication.
Use a secure random number generator, SecureRandom, to initialize any cryptographic keys, KeyGenerator. Use of a key that is not generated with a secure random number generator significantly weakens the strength of the algorithm, and may allow offline attacks(Source Google Developer Site).
Comments
top android app development companies | top mobile app development companies
Thanks, that's extremely good information, cheers.
android app development perth | android app development sydney
Altorum Leren, a leading IT, Services Company, specializes in Technology Service Provider, Software Development, Cloud Computing Services, UI/UX Design Services, Internet of Things Services, Artificial Intelligence Services, Blockchain Solutions, DevOps as a Service, Front End Web Development, Back End Web Development, Web & Mobile App Development and more. https://www.altorumleren.com/